CTI Transaction Flow
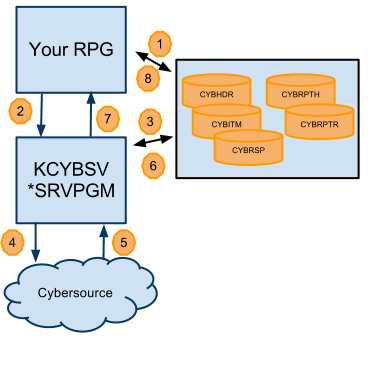
- Your RPG is a program within your application that first occupies the KCYB DB2 tables with relevant transactional information. The DB key from writing those records is then passed to the KCYBSV *SRVPGM. Credit card numbers and security numbers ARE NOT stored in DB2 tables for PCI compliance reasons and are instead passed as parameters on the call to the exported sub procedure.
- The KCYBSV *SRVPGM sub procedure is invoked.
- KCYBSV reads the DB2 tables to compose the XML documents.
- KCYBSV communicates with the remote web service including the digital signing of the transaction and all encryption.
- KCYBSV receives the response from the Cybersource web service and parses the response.
- KCYBSV places the parsed XML into the corresponding DB2 tables.
- Control is passed back to Your RPG program.
- Your RPG program can then read the response from the DB2 tables and relay relevant information back to the user (if it is an interactive program)